How to set user password expiration time on Linux with Ansible?
I'm going to show you a live Playbook with some simple Ansible code.
I'm Luca Berton and welcome to today's episode of Ansible Pilot.
Ansible user password expiration
- ansible.builtin.user
- Manage user accounts
Today we're talking about the Ansible module user.
The full name is ansible.builtin.user, which means that is part of the collection of modules "builtin" with ansible and shipped with it.
It's a module pretty stable and out for years, it manages user accounts and supports a huge variety of Linux distributions.
For Windows, use the ansible.windows.win_user module instead.
Linux password aging policy
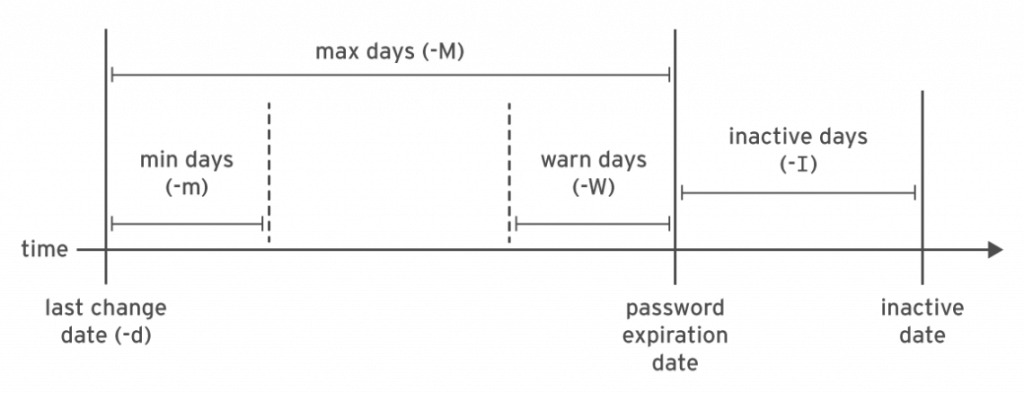
This schema represents the Linux password aging policy.
Let me highlight that the Ansible native module user is able to set only the min days -m and max days -M parameter.
Max days set password policy for requesting password should be renewed, for example in every 90 days.
Min days set the minimum days should be waiting for changing the password again, for example after 7 days from the last change.
To disable password aging specify the value of 99999.
For the other parameters, you need to rely on the chage command-line utility or via the Ansible shell module.
Parameters
- name string - username
- password_expire_min integer - Linux min days validity (-m)
- password_expire_max integer - Linux max days validity (-M)
This module has many parameters to perform any task.
The only required is "name", which is the username.
In the password_expire_min parameter you specify the value of the min days validity.
In the password_expire_max parameter you specify the value of the max days' validity.
Please note that these parameters are Linux only.
## Playbook
Set user password expiration time with Ansible Playbook.
Pleasee note: [user module password_expiry_min bug and workaround](/articles/ansible-troubleshooting-user-module-bug).
code
- user_expiration.yml
``yaml
---
- name: user module Playbook
hosts: all
become: true
vars:
myuser: "example"
tasks:
- name: password expiration
ansible.builtin.user:
name: "{{ myuser }}"
password_expire_min: 7
password_expire_max: 90
`
execution
``bash
$ ansible-playbook -i Playbook/inventory user\ expiration/user.yml
PLAY [user module Playbook] **
TASK [Gathering Facts] *
ok: [demo.example.com]
TASK [password expiration] *
changed: [demo.example.com]
PLAY RECAP *
demo.example.com : ok=2 changed=1 unreachable=0 failed=0 skipped=